GDB
Challenge Binary
After downloading the above file go to the directory where the file is present and type chmod +x crackme in the terminal to make the file executable.
First, load the file into gdb by typing gdb filename in your terminal. For this, you have to be in the directory where the file is located. Here my filename is crackme. Once the file is loaded, to see all the functions defined in the file type info functions
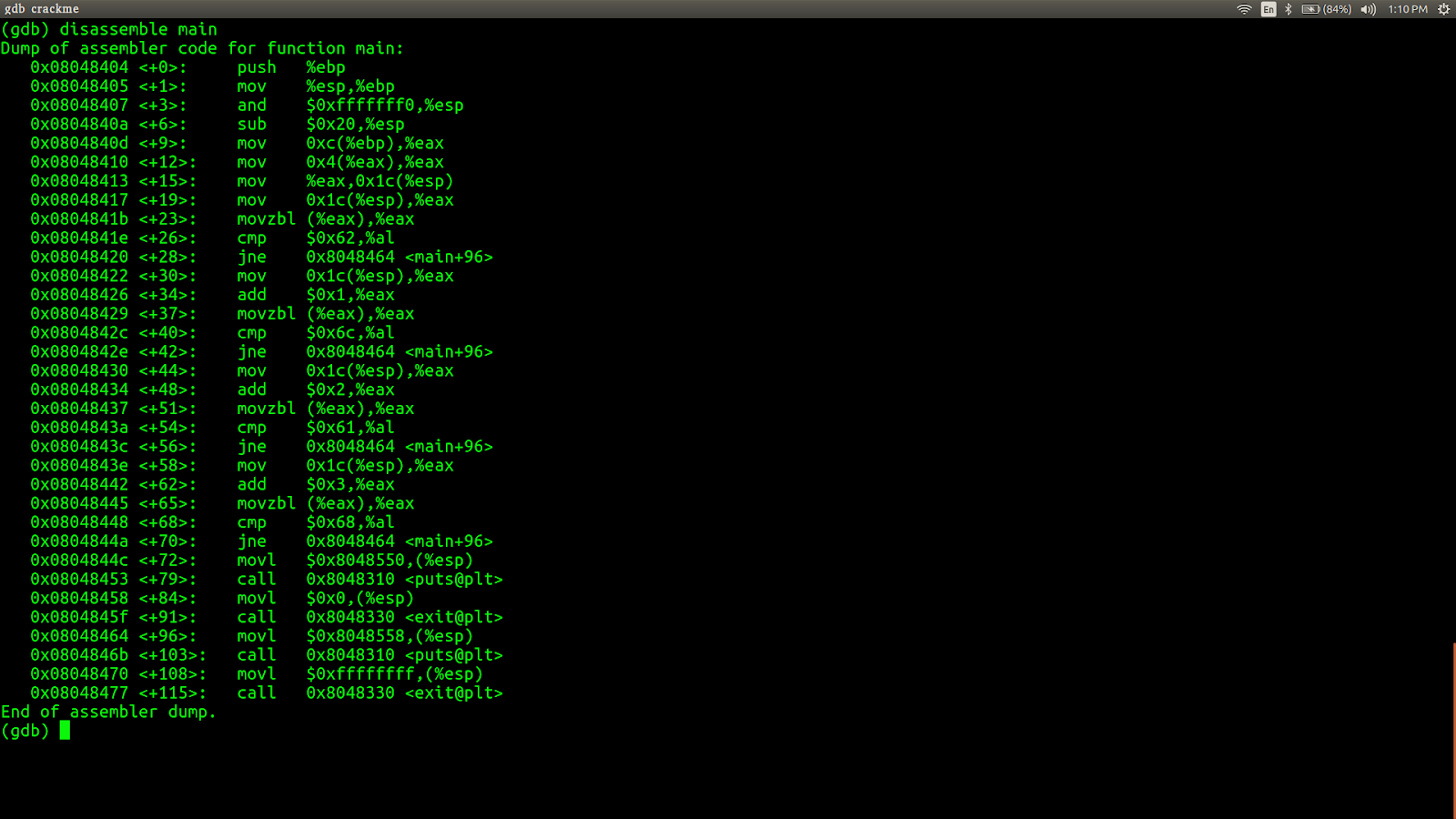
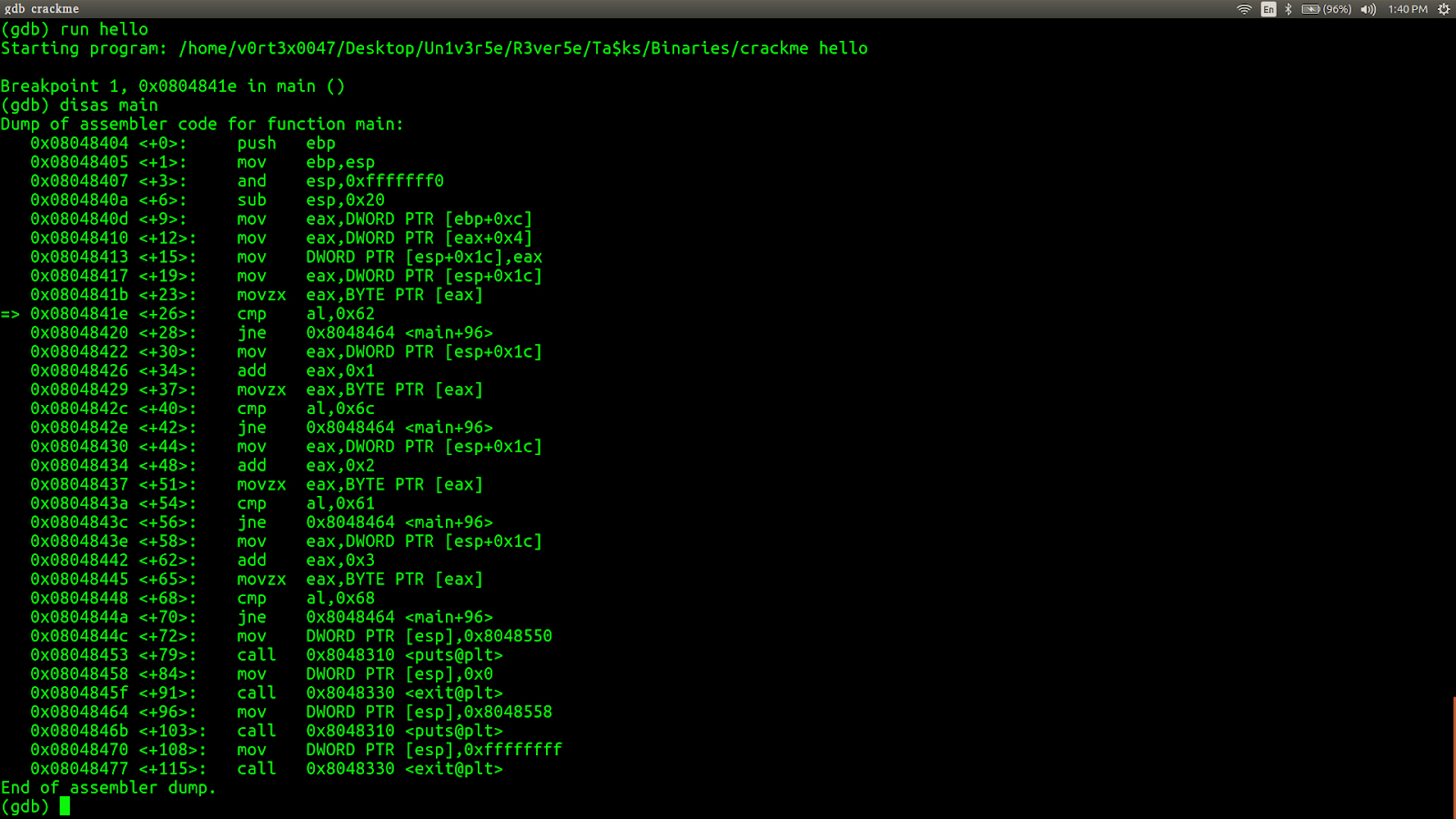
We have the main function defined. Let's see the disassembly of the main function by typing disassemble main. We get something like this
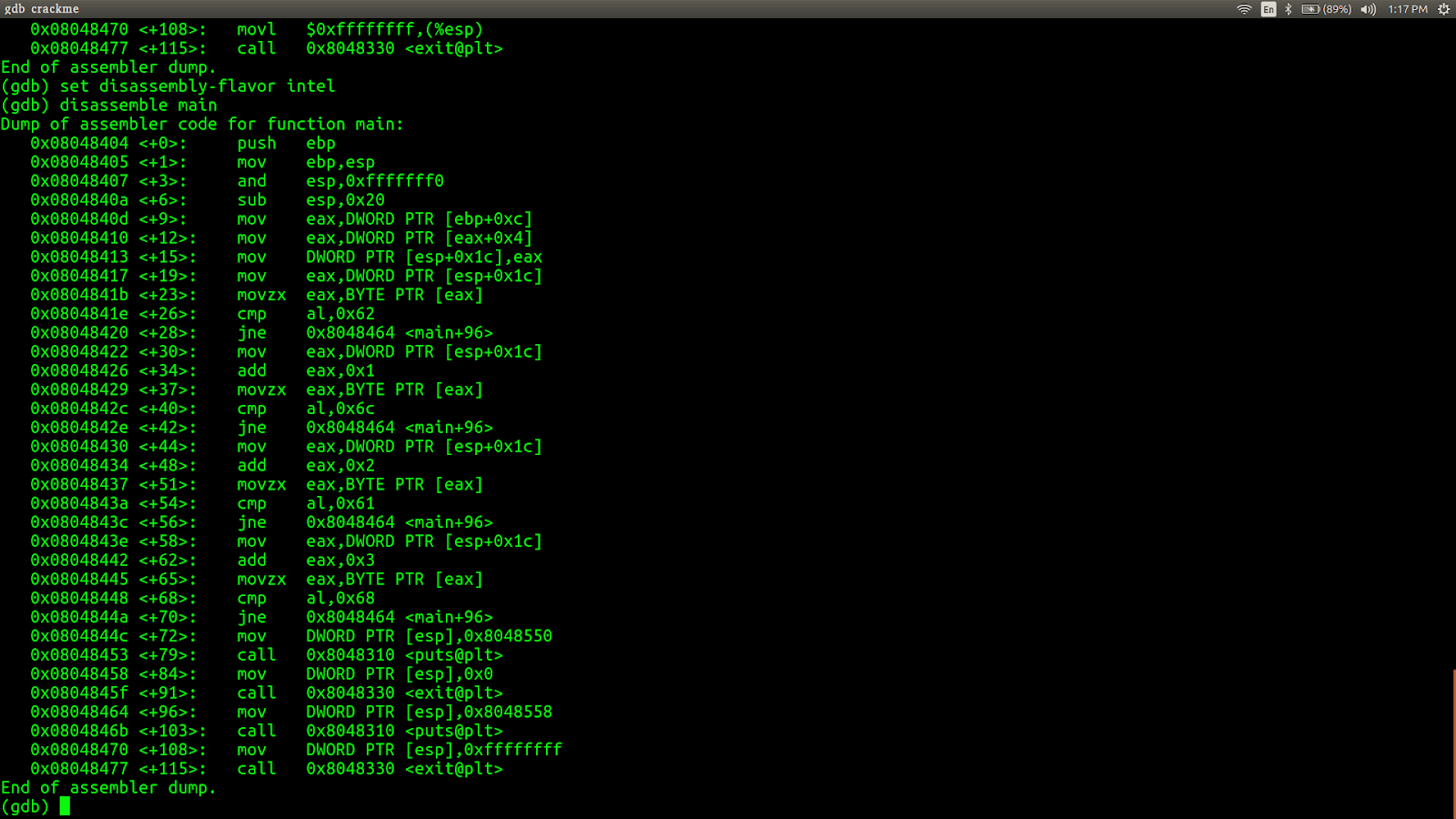
Now the disassembly of the main function is in AT&T format, we'll change that into Intel format by typing set disassembly-flavor intel (I prefer Intel format :D ).
Now let's see the disassembly of the main function by typing disassemble main. It will be like this.
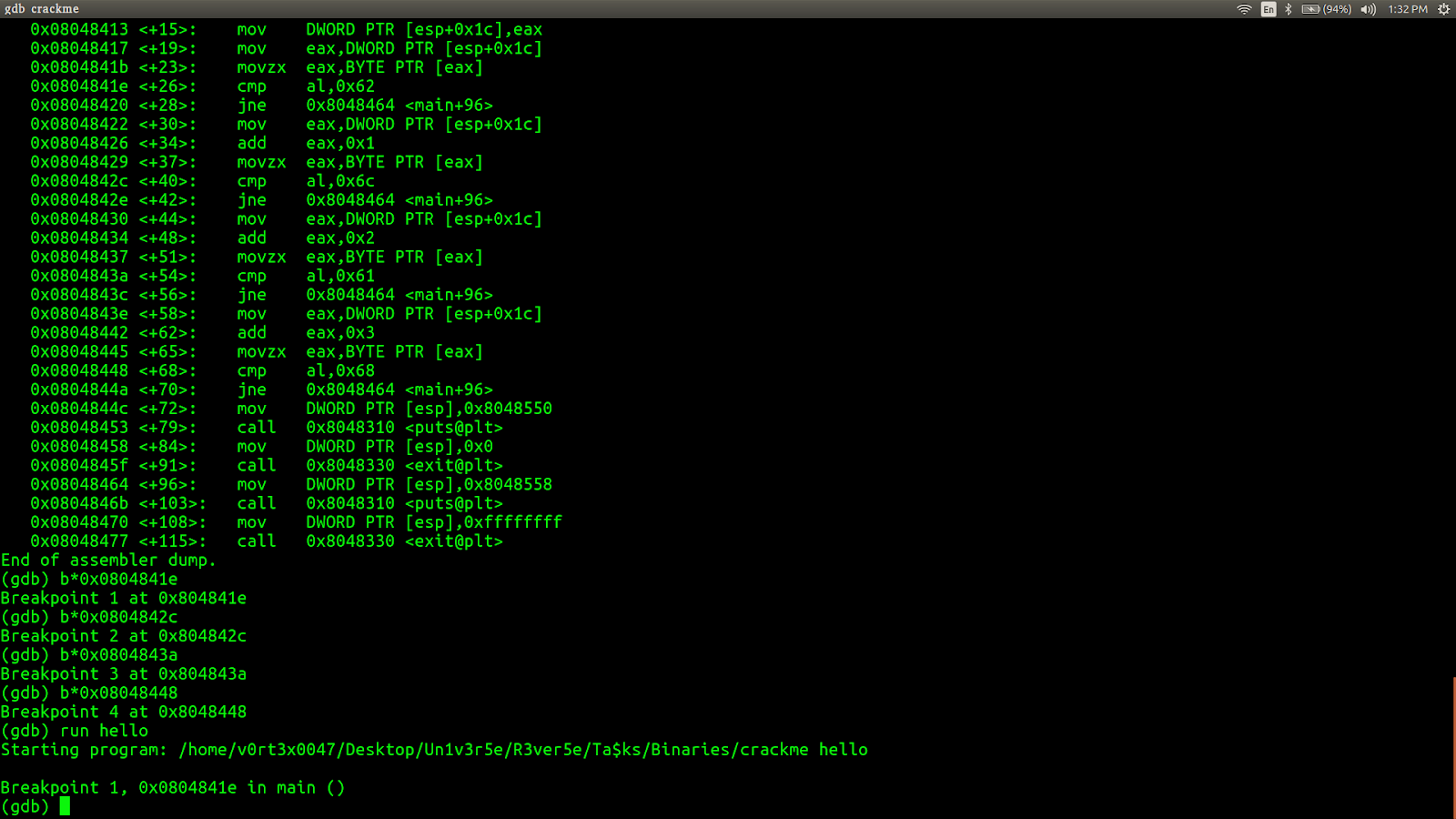
On observing the disassembly of the main function, we can say that there are 4 compare statements. Let's see what is actually happening at those compare staetments by putting break points at those 4 locations. To put the break point type b*address.The corresponding addresses are to the left side of the instruction(something like 0xaaaaaaaa).
Now let's run the program by giving some random input (say 'hello') . Type run hello to run the program with 'hello' as the input.
Now the program is halted at the 1st breakpoint. Now type disas main.
The small arrow indicates the next instruction to be executed. The comparison is between al and 0x62. Let's see what is in al. To see what is present in al type print $al.
It gives us 104 (0x68 hex ).It is nothing but the ASCII value of the 1st byte of our input (hello) which is 'h'. It is being compared with 0x62 (98) ASCII value of letter 'b'.Let's manually see what happens next.Type ni to proceed to the next instruction. As our input doesn't match with 0x62, jne 0x8048464 this jump instruction is executed and the program control jumps to the instruction at 0x8048464.(Type x/x $eip whenever you want to see what instruction is going to be executed next or where the program control is right now. or just type disas main)
0x08048464 <+96> : mov DWORD PTR [esp],0x8048558
0x0804846b <+103>: call 0x8048310 <puts@plt>
0x08048470 <+108>: mov DWORD PTR [esp],0xffffffff
0x08048477 <+115>: call 0x8048330 <exit@plt>
These 4 instructions will be executed, "You Lose" is printed on to the screen and program exits normally.
Now we have concluded that our 1st letter must be 'b'. Similarly, there are 3 more compare statements.
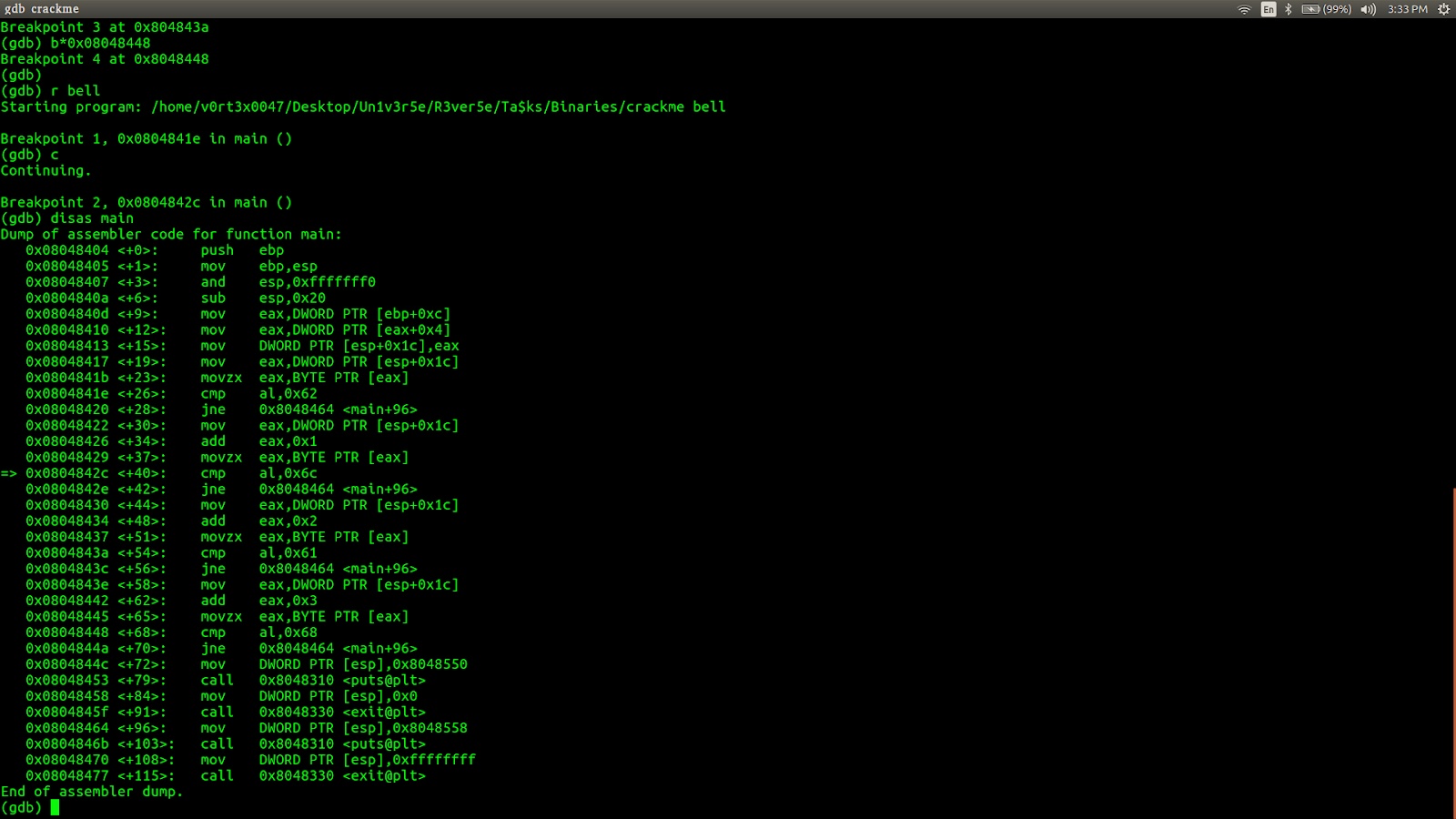
Let's run the program again by giving 'b' as the 1st letter in our input(say 'bell'). Type r bell .
Now as the 1st letter of our input is 'b', jne 0x8048464 this instruction is not executed and it successfully goes to the next breakpoint.
Type c continue and then see where our program control is.
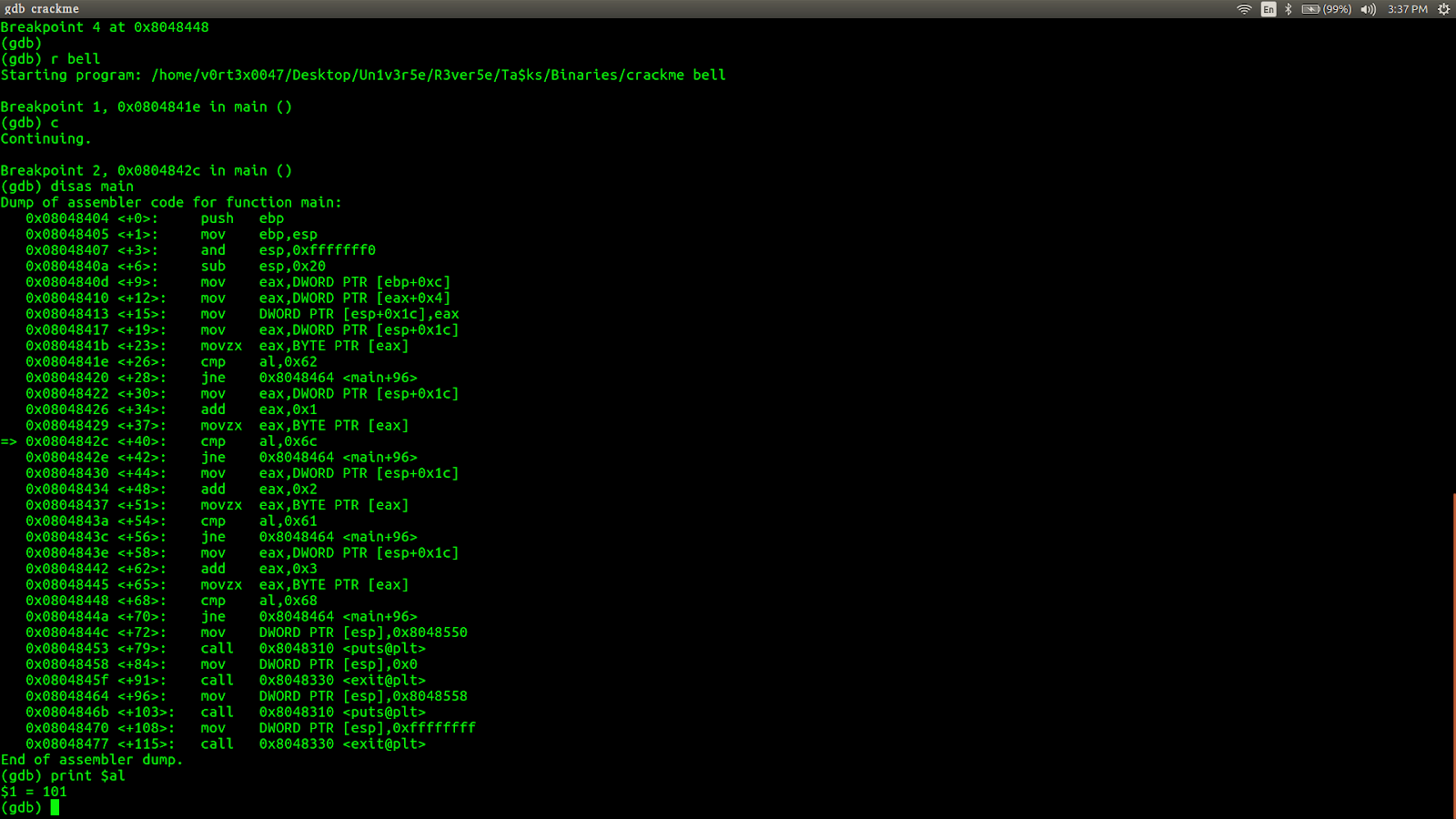
Now our instruction pointer is at the 2nd breakpoint. Here lets see what is in al. Type print $al.
We get 101 (0x65), that is the ASCII value of 'e' which is the 2nd letter of our input. It is being compared with 0x6c (108), ASCII value of 'l'. So our 2nd letter has got to be 'l'.
Similarly, there are 2 more compare statements which take the 3rd byte and the 4th byte of our input and check them with 0x61(97 ASCII value for 'a') and 0x68(104 ASCII value for 'h') respectively.
So our input must be "blah".
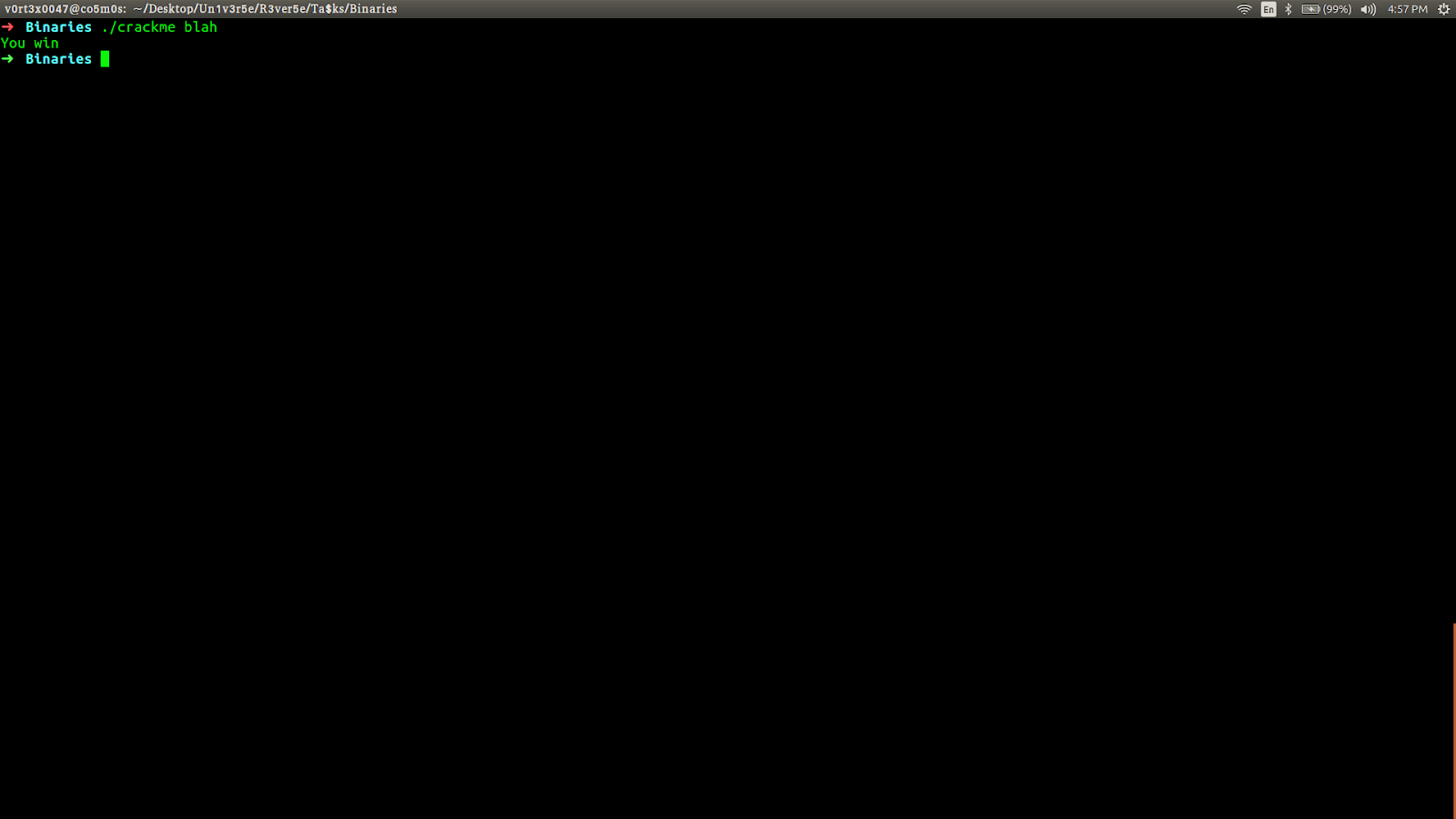
Now get out of gdb by pressing ctrl+z. Then run the file by giving 'blah' as the input. Type ./crackme blahto run the file with 'blah' as input.
The challenge is complete. "You win"
Tasks
Now you have reached a crucial point. This is what you were waiting for.This is the first real RE challenge that you will be facing.
You are going to be provided with the bomb labs binary. You need to pass the stages 1 - 6 to defuse the bomb. And there is also a secret level.
Tools that can be used :
- Gdb
-
python
-
Additionally you can store the inputs of the stages that you have already found out in a file let's assume it is
inp. Now the next time you are running the binary you can run it asr < inpin gdb and you can save the hassle of typing the previous inputs
Also keep in mind that you can't patch or change the values of any registers at any point of time. The solution requires you to find out exactly the password of each stage.
Submit the passwords of each stage as a single file which when run
./bomblabs < inp should clear all the stages.