Bluetooth¶
Bluetooth is a technology for wireless data exchange over short distances with the help of RF signals. It uses short wavelength Ultra High Frequency (UHF) radio waves to transmit data. They use the ISM band (industrial, scientific and medical radio) using a frequency between 2400 GHz and 2483 GHz.
Working¶
Bluetooth uses a Frequency Hopping Spread spectrum (FHSS). This technique enables transmitters change frequency every 1600 ps. Many devices make use of the full radio spectrum to communicate so that it's highly unlikely for two devices to interfere with each other on the same frequency.
A device connected to another via Bluetooth form a piconet or a Personal Area Network (PAN). The general topology is of the master slave type with one master and 7 different slaves. The devices involved in the piconet hop the frequency together in a pseudo random manner, seeded by the master's MAC address. The timing is decided through the master's clock.
-
The potential slave device has to be put in discovery mode.
-
This enables devices to listen on the 32 designated inquiry frequency channels for messages and respond to them.
-
The potential master device sends out inquiry packets on those inquiry channels. After exchanging messages, the devices eventually reach connected mode and form a piconet.
BLE (Bluetooth Low Energy ) was introduced in Bluetooth 4.0. Since its inception, it has become very common in smart devices. BLE is explicitly designed for devices with power constraints and therefore has a very large market presence. The difference between BLE and Bluetooth Classic are as follows:
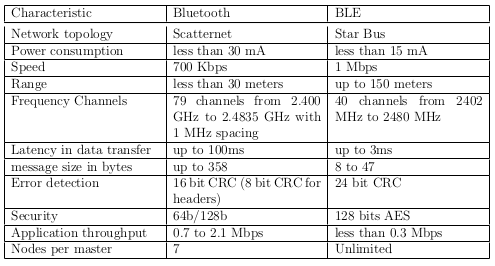
Now, let's look at the BLE stack. It basically consists of the Application, Host and Controller. The second two interacts through the HCI interface. The Physical Layer is responsible for signal modulation, demodulation, and for calculating the hopping pattern for FHSS. The Link Layer manages several things such as the Bluetooth address, encryption and connection initiation.
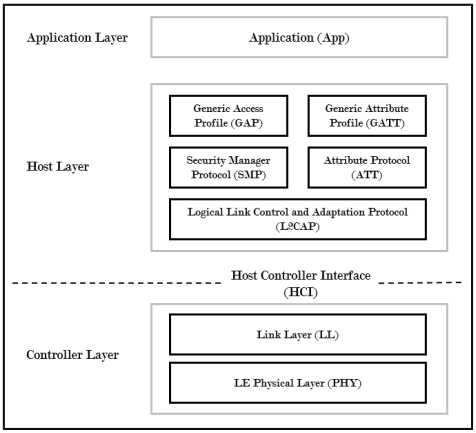
In the Host Layer GATT is the component which manages the data exchange and performs operations like read, write and error handling. It handles the data by categorising in the following manner:
- Entire data is enclosed within profiles each containing services.
- Services have a UUID (universally unique identifier).
- Each service further encloses several characteristics which also have UUIDs.
Bluetooth Security : Overview¶
As Bluetooth is a wireless networking setup, security is a great concern. Especially the automated connection handling nature of Bluetooth benefits adversaries to gain information without permission. BLE offers several security levels and modes :
- Level 1 supports unpaired communication with no security at all.
- Level 2 supports AES Cipher based Message Authentication Code (AES CMAC) encryption for unpaired communication
- Level 3 supports encryption and requires pairing
- Level 4 supports Elliptic Curve Diffie-Hellman Ephimeral (ECDHE) exchange instead of AES-CMAC
Among the above the Level 4 is the most secure. BLE also provides security modes which further enhances the security.
Reference¶
ELVIS wiki [2020] [online] Available at: https://wiki.elvis.science/images/2/2d/Pentesting_in_IoT_Bluetooth_Sniffing.pdf [Accessed 27 December 2020].