Network Protocols and the OSI model¶
Network Protocols¶
They are a set of rules and regulations to manage the communication between any systems in a network. Each layer has a set of protocols placed to manage the data exchange and effective functioning of the network as well. Data units are transferred across each layer of the network on the basis of the defined protocols.
The OSI model¶
It is a conceptual idea that gives a standardisation to the communication function to a computer system without regard to its internal structure or technology. The model partitions a communication system to seven layers, where each layer serves to the layer above it. This is to enable the operability of diverse communication systems and networks together. This is achieved by standardising all systems with protocols and regulations for each layer of a network. Each layer serves in its own ways to establish and ensure communication system to work efficiently. While one layer provides a path for the transfer of data from one node to another above which applications will operate upon, while it calls the next lower layer to receive and send packets which comprise of the data of that session.
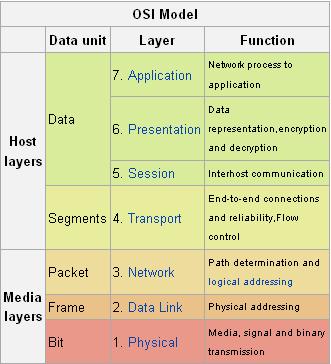
A system is broadly classified into seven layers as
- Physical Layer
- Data link Layer
- Network Layer
- Transport Layer
- Session Layer
- Presentation Layer
- Application Layer
Each layer serves a certain purpose that is necessary for the effective functioning of the network.
1. Physical layer : This layer generally represents the medium through which the network data is transferred. For example, an electrical cable or an optical cable provides a physical medium or platform through which all the data is transferred.
2. Data link layer : Data link layer is generally the means by which the transport of data happens across a physical network. Bridges and switches are the physical devices that initiate and act as the means of transfer. The common protocol used in this layer is Ethernet. MAC address provides an addressing scheme to identify physical devices.
3. Network layer : This layer basically routes data between physical networks and assigns logical addresses to network hosts. They are also basically responsible for handling packet fragmentation and error detection. Protocols like ICMP are present in this layer.
4. Transport layer : This layer provides a control flow between two hosts in a network. It acts as a mean for transferring a variety of data through the network maintaining the quality.
5. Session layer: It is used mainly to manage the sessions between two computers. It mainly does managing operations like terminating sessions gracefully etc. Example protocols are NetBIOS, NWLink.
6. Presentation layer: It encodes/decodes through different forms of encryption/decryption for securing the data. This is basically done to transform the data received to a format that can be read by application layers.
7. Application layer: This provides the details for the end user to access network resources. Examples are HTTP, SMTP,FTP,Telnet.
Data Encapsulation¶
In order to facilitate the conversation between different layers in a network, each layer in the stack adds a footer or header, the way that different layers in OSI model communicate is through data encapsulation. Protocol Data Unit (PDU) created by the encapsulation protocol includes the header and footer information to the packet data.
Protocol data unit (PDU)
It is information that is transferred among the peer entities of a computer network as a single unit. It may contain user data, network addressing or control information. In the communication protocol stack, each layer has a protocol that is made in order to adapt to the specific type or mode of data exchange. For eg; TCP implements a connection-oriented transfer mode, and the PDU is called a segment, whereas, at a lower layer, the IP has a PDU of packet.
Hence packets are nothing but are PDUs that are transferred and are complete with the header and footer.
Now let us look into some common network protocols :
ARP¶
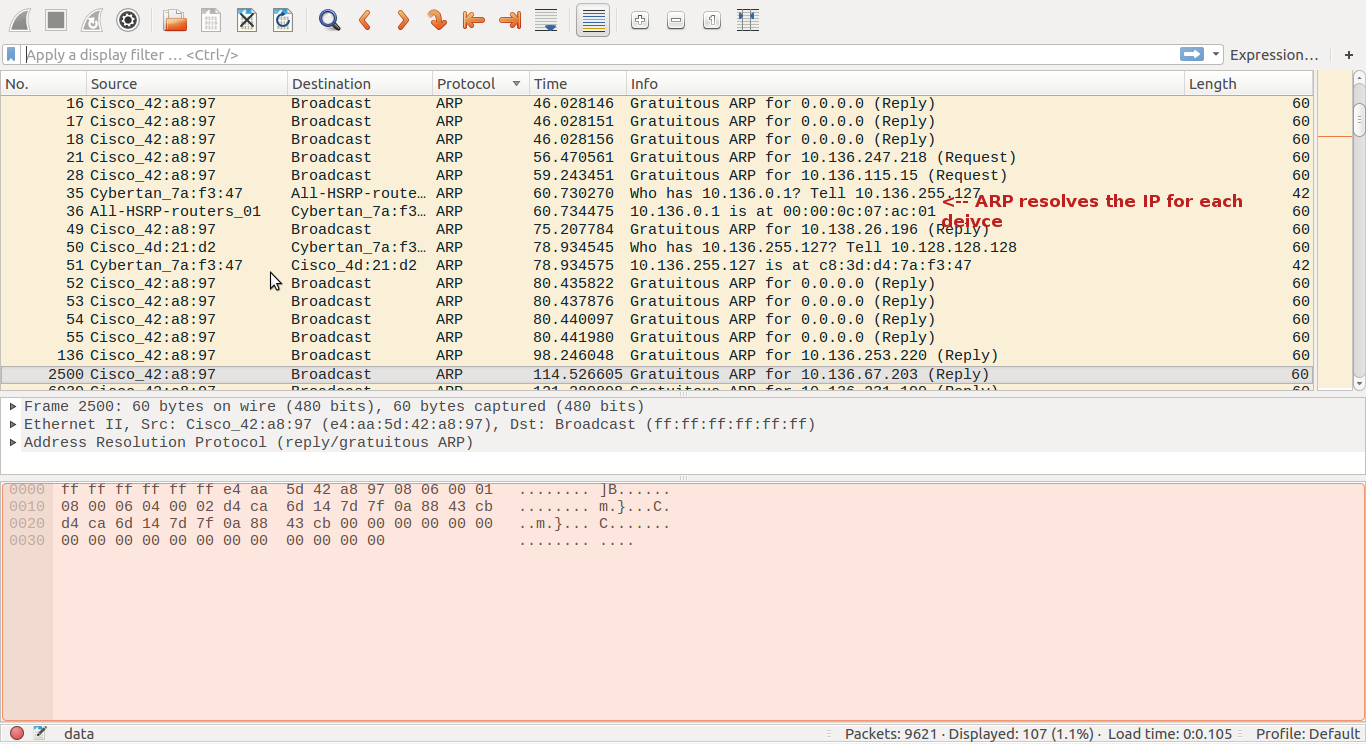
In order for devices that are connected to each other with a switch into a single network, a physical address is used as a reference for every device connected. ARP determines which MAC address (physical address) corresponds to a particular IP address. ARP sends two kinds of packets (ARP resolution,ARP request), where a broadcast packet is sent to every device in the network and then wait for the response from the correct client.
MAC Address
The MAC address of a device is the UID assigned to a NIC to enable data transmission in the data link layer of a network segment. This address is often assigned by the manufacturer and is stored in the device hardware.
IP¶
It basically delivers packets between hosts based on the IP addresses in the packet header. It is the principal protocol in the Internet protocol suite and relays data across the network.
TCP¶
TCP or transmission control protocol is a transport layer protocol that provides error-checked delivery bytes between hosts connected via a network. TCP provides a reliable data stream service hence major applications and application layer protocols that need assurance of data integrity use TCP, unlike UDP which is also a transport layer protocol. Applications that do not require reliable data stream service may use the User Datagram Protocol (UDP). The communication between two hosts is established by the three-way handshake.
Three-way handshake¶
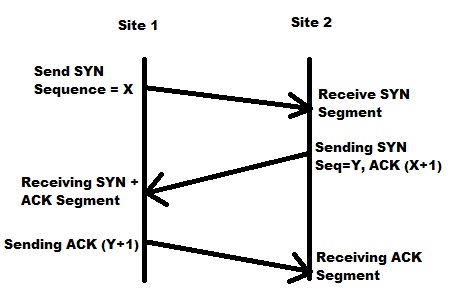
Consider the scenario where Alice(host1) is trying to connect via a TCP connection with Bob(host2). The connection is established after three separate steps:
- The first host Alice sends a SYN message ("Synchronise") with a particular sequence number x to Bob.
- Bob replies with a SYN-ACK(Synchronise-Acknowledgement) message with its own sequence number y and acknowledgement number y+1 to Alice.
- Alice replies with an acknowledgement (ACK) message with acknowledgement number y + 1, which Bob receives to which he doesn't necessarily need to reply.
Note
In this handshake the synchronise messages act as service requests from one host to another, while the acknowledgement messages return to the requesting server as an acknowledgement to the request message.
UDP¶
UDP is also a transport layer protocol and an alternative to the TCP. It is used for establishing connections between applications on the network that have more data loss. Unlike TCP, UDP doesn't provide any error and flow control mechanisms. Hence UDP is implemented when the connection required has to be fast and the applications can tolerate a certain amount of data loss.
ICMP¶
Internet control message protocol is a protocol used by network devices like routers to send an error message that a requested service is not available or that the device is currently unreachable.
Tip
In packet capture with ICMP packets, external data can be sent as payload once the packet data is sent. The payload is appended to the packet data of each packet. By using scripts we can extract the payload from the PCAP file. In CTFs often challenges come where certain files like a ZIP or PNG image is broken and send as payload through each ICMP packet. This data can be extracted by scripting.
HTTP¶
Hyper Text Transfer Protocol1 is the protocol to exchange or transfer hypertext. It is an application layer protocol and is the foundation for data transfer for the World Wide Web.
Click the below link to see a write up of a challenge from a CTF which involved analysis of a PCAP file using Wireshark.