Image Forensics¶
What is Image Forensics?¶
To keep it very simple and straight, Image Forensics is a specific branch of cyber forensics which deals with a various number of attacks.
Some of them include:
-
The authenticity of an image
- When we speak of authenticity, we are actually talking whether the image is properly structured or not. Sometimes the data preserved inside may be tampered. Forensic analysts are required to recover this tampered data to its original state.
-
Detection of possible forgeries etc.
- Detecting forgeries of images is a really big thing in the tech industry because many confidential images or files may be stolen or unlawfully used for criminal purposes.
So let us look into some of the very basic definitions of the technical terms used in this field to better understand the upcoming topics.
File Signature¶
A typical file signature is something which defines the nature of a file and also tells us about the specific features of the particular file. This is also called as the file header or sometimes as the checksum.
So let us look at some examples:
-
PNG -> 89 50 4E 47 0D 0A 1A 0A
-
ZIP FILE -> 50 4B 03 04 or 50 4B 05 06
The 'hex' values shown are also called as magic numbers.
Chunks¶
Chunks are nothing but fragments of information used by different multimedia formats like PNG, MP3 etc. Each chunk has its own header. The header usually describes the type and size of the chunk.
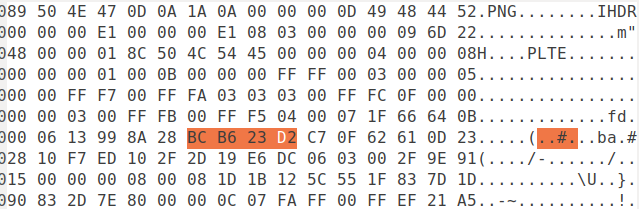
How important are chunks ?
So let us consider that you are trying to open an image using an MP3 player. Will the player open the image? No, right. It'll give me an error message. Every application has a decoder which checks the type of the chunks given. When it recognizes that the given chunks are supported, it tries to give the desired output. So whenever it comes across chunks of unknown format, it triggers an error message stating "Unsupported File Format"
Checksum¶
Checksum is an integral value which represents the sum of correct digits in a piece of data. Checksums help us to check the data integrity of a file which is transmitted across the digital network. There are many checksum algorithms. Checksum algorithms are employed in various cybersecurity concepts like fingerprinting, cryptographic hash functions etc.
Lossless Compression¶
The name itself tells that there will be no loss of information when a set of data is compressed. the lossless compression technique is used for reducing the data size for storage. For example, png is a lossless compression and the advantages of a lossless compression file format are that there is no loss of quality each time it is opened or saved.
Lossy Compression¶
In lossy compression, it involves loss of information from the original file when data is compressed. Lossy compression can result in the smaller size of the file but it also removes some original pixels, video frames, sound waves forever. For example, JPEG is lossy compression and the disadvantage is that each time the image is saved it loses some amount of data and which simultaneously degrades the image quality.
Metadata Of An Image:¶
Image metadata is a text information which gives information about the details associated with the image. Some of these details are: + Size and resolution + The author of the image + The GPS data of this image + The time when the image was taken, last modified etc.
So now let us look at the file format of a PNG image:
Portable Network Graphics (PNG)¶
A PNG is a graphical file format of an image which supports lossless compression.
Magic Number -> 89 50 4E 47 0D 0A 1A 0A
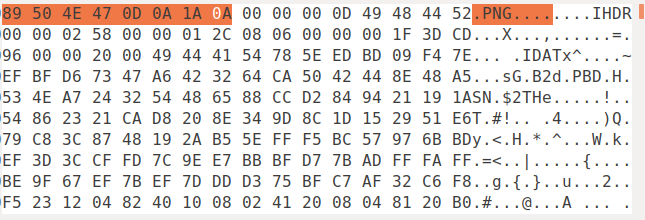 So now let us look at the critical chunks of a PNG image:
So now let us look at the critical chunks of a PNG image:
Critical chunks¶
IHDR -> Describes image dimensions, color type, bit depth etc. It must be noted that this must be the first chunk (always).
PLTE -> Contains the list of colours.
IDAT -> Contains the image data.
IEND -> Marks the end of the image.
Ancillary chunks¶
Ancillary chunks can be otherwise called as optional chunks. These are the chunks which are generally ignored by decoders. Let us look at some examples:
bKGD -> Gives the default background colour.
dSIG -> This chunk is used to store the digital signature of the image.
pHYS -> Holds the pixel size and the ratio of dimensions of the image.
All the ancillary chunks start with a small letter.
Executable and Linkable Format (ELF)¶
The ELF file format is standard file format for executables, object codes, core dumps etc. for any UNIX based system.
Magic Number -> 7F 45 4c 46
The file header of an ELF file defines whether to use 32-bit or 64-bit addresses. ELF files are generally analysed using a tool called readelf.
ZIP¶
Zip is actually a file format which supports lossless data compression. This file format achieves the compression of a file(s) using a number of compression algorithms. DEFLATE is the most used compression algorithm. Zip files have the file extension .zip or.ZIP.
Magic Number -> 50 4B 03 04 and 50 4B 05 06(for empty zip files)
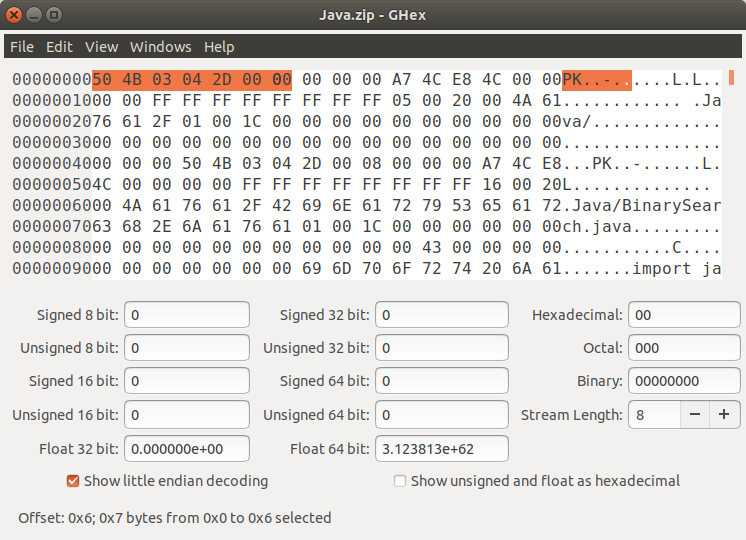
Zip files can be extracted using this command in the terminal.
$ unzip file_name.zip