CBC¶
Cipher Block Chaining (significantly known as CBC) is a mode of encryption used in block ciphers. It is an advanced form of block cipher encryption and also more secured when compared to ECB. This mode uses a random block of bytes known as Initialization Vector (IV) to ensure randomization of encryption. It is important to use IV only once to ensure security.
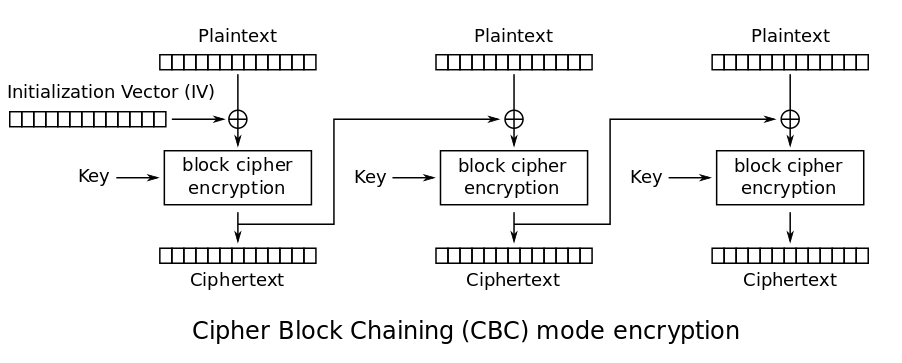
Encryption:¶
CBC is one of the most popularly used mode of encryption in AES. Unlike in ECB mode, in CBC mode, encryption of one block of plaintext is dependent on the previous block. Each block of plaintext is XORed with the previous block of ciphertext, for the first block it is XORed with IV(16 bytes) and then sent through the whitebox. So, change in one single byte changes the entire ciphertext. Hence, eavesdropper can’t attack the data easily.
C[i] = E(Pt[i] ^ C[i-1])
C[1] = E(Pt[i] ^ IV)
Advantages over ECB:¶
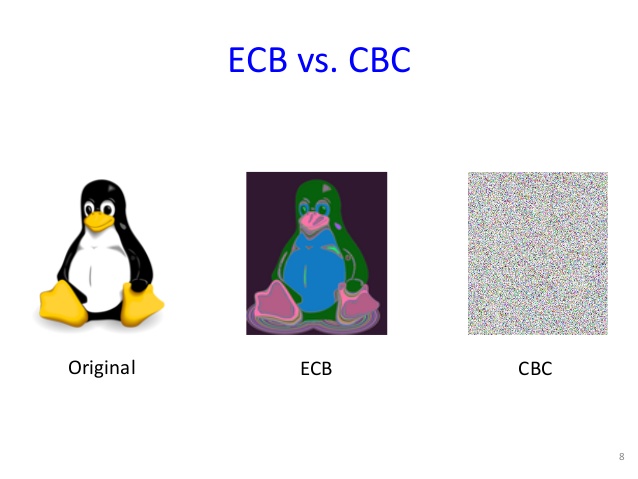
Dependency of one block encryption over the previous one ensures that traces of similar data aren’t left behind, whereas in ECB, change in a byte changes only the corresponding block i.e encrypting 2 blocks that contain same plaintext gives the same ciphertext in ECB. This gives a pattern to the attacker whereas in CBC this doesn’t happen.
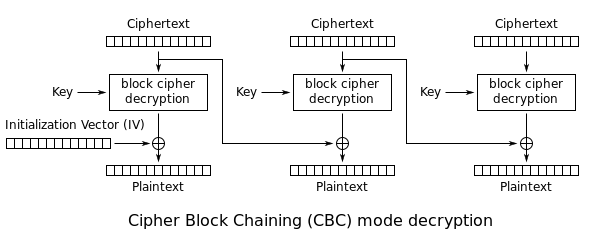
Decryption:¶
Decryption is just the reverse. Each block of ciphertext is sent through the whitebox and then XORed with the previous block of ciphertext to recover the plaintext. So, one need not decrypt the previous block to get the required block of plaintext.
Pt[i] = D(C[i]) ^ C[i-1]
Pt[1] = D(C[1]) ^ IV
Attacks possible:¶
IV reusing might lead to leakage of information regarding the first block of plaintext. However the rest are unaffected. It is also vulnerable to attacks like bit flipping attack, padding oracle attack etc.